Hurricane Katrina and now Hurricane Harvey are natural disasters that disable everything around them and have caused the nation to shake. They cause the communities to come together and truly shine, especially through the powers of the small businesses that link up for a greater cause. We have constantly found ourselves in shock and in a state of sadness when he view the aftermaths of natural disasters, and it sets up our nation for the vision of how technology can better help us in preventing the actions of natural disasters. It also puts into play how businesses rebound from catastrophes, such as Hurricane Harvey, in terms of resetting up their business and IT services. Can IT really help companies recover and help resolve the community? It has the ability to do that and much more.
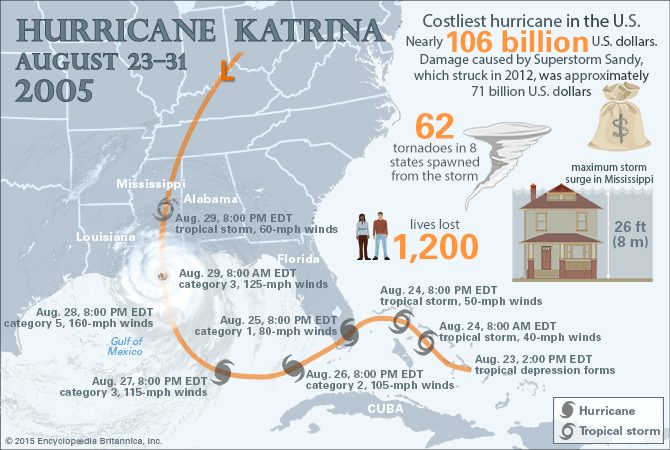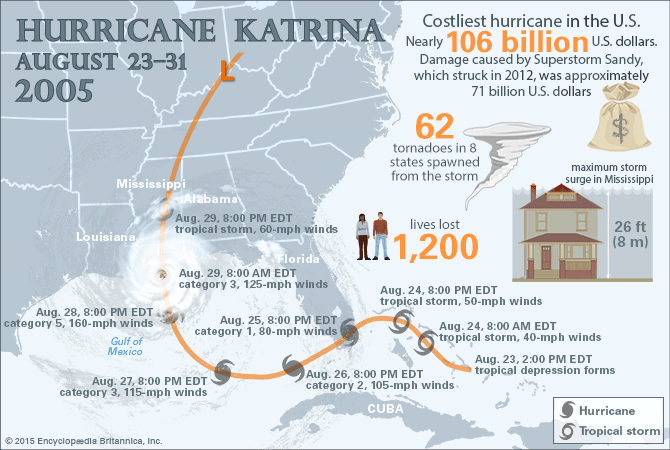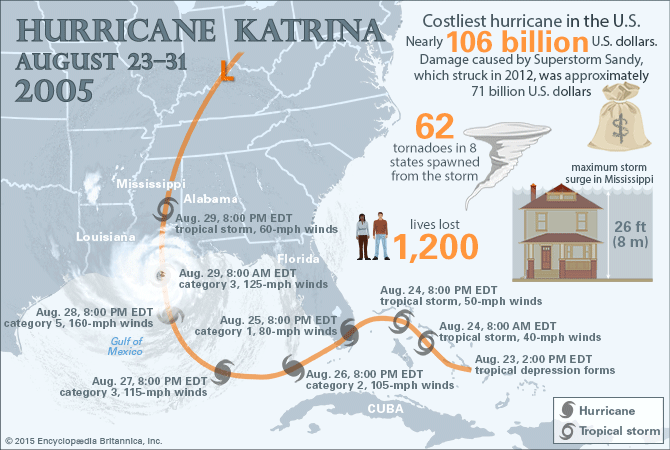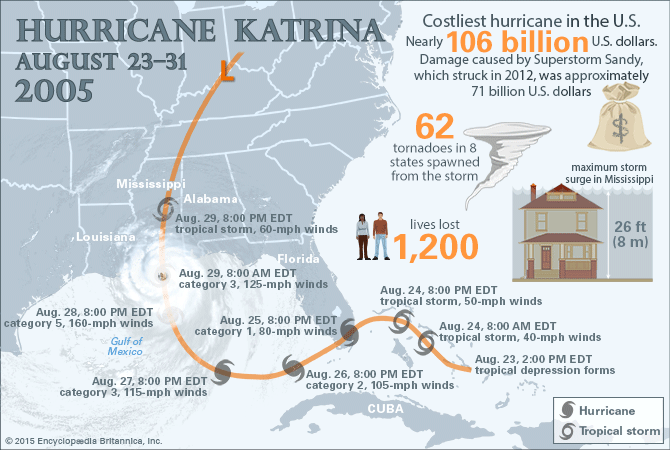
Source: https://www.britannica.com/event/Hurricane-Katrina
Information Technology has always been the tool used to advance our society. We depend on both information and technology as a source of national separation, competing with other countries on who has the most advanced set of technological tools to innovate. In times of natural disasters, we need to take a step back to the fundamentals of IT to figure out how small businesses recover from natural disasters, or in this case, Hurricane Harvey. Now in most scenarios, if not all, there is a lot of support going into the communities, commonly raising money for business’, for people to get their homes back and lives to return back to normal and what not. An IT department is great for businesses making a recovery from any situation, and sometimes it is even important to make sure you have disaster occurrence insurance, especially if the location you are in is common for these disasters. You should always make sure, with or without your IT services, that your information is secured, backed up and saved so that re-launch is not the most dreadful part of recovering from an event. Of course on top of the IT costs you have to worry about physical building costs and interior and what not, part of your personal expenses and government/city expenses as both will take part in recovery of your business. So try your best to minimize these costs. Recovering information when it is not backed up is very costly and a hard task at that, trying to work around damage is not an easy task when it comes to data which is why layers of fail-safes are important to any business. Put yourself in a situation where you can depend on IT and not have to be a small business looking for IT services last minute. Consult with us today so that we can better prepare your business for situations such as these.
-
Source: https://goo.gl/h3Laz6
Our thoughts are with the people whom have been affected by hurricane Harvey. To donate, please visit the American Red Cross or simply click here